News
Technology News from Dynamic Alliance
Enhancing Your Network Security and Maintenance for a Resilient Business

In today’s ever-evolving digital landscape, enhancing network security
and maintenance is paramount to safeguarding businesses against a myriad
of cyber threats. A proactive approach to network security involves staying
abreast of the latest threat intelligence. By continuously analyzing and
understanding emerging risks, businesses can fortify their defenses and
preemptively address vulnerabilities before they are exploited.
Read on to learn more about Network Security and Maintenance and the
following topics:
- MFA
- Security Auditing
- Remote Monitoring Tools
- Comprehensive Disaster Recovery Plan
Multi-Factor Authentication
Implementing multi-factor authentication (MFA) is a crucial step in
bolstering access control. In a world where passwords alone may not
suffice, MFA adds an additional layer of security, requiring users to
verify their identity through multiple means. Whether through biometrics,
smart cards, or one-time passcodes, MFA significantly raises the bar
for unauthorized access. Businesses embracing MFA not only enhance
their security posture, but also instill a culture of vigilance
among users, fostering a collective commitment to cybersecurity.
Security Auditing
Conducting regular security audits is an indispensable practice in
maintaining a resilient network infrastructure. These audits, often
conducted by cybersecurity professionals, delve deep into the
network architecture, identifying potential vulnerabilities and
weaknesses. By addressing these issues promptly, businesses can
shore up their defenses, creating a proactive shield against potential
cyber threats. Security audits not only serve as a diagnostic tool
but also as a strategic investment in the long-term security and
stability of the organization’s digital assets.
Remote Monitoring Tools
In the realm of network maintenance, proactive monitoring emerges
as a linchpin for identifying and mitigating issues before they
escalate. Remote monitoring tools provide real-time visibility into
the health and performance of the network., This continuous oversight
allows IT teams to detect anomalies, unusual patterns, or potential
security breaches promptly. The ability to respond swiftly to emerging
issues is instrumental in maintaining a secure and resilient network
infrastructure.
Effective patch management compliments proactive monitoring by ensuring
that all software and systems are up to date with the latest security
patches. Cybercriminals often exploit known vulnerabilities, making
timely patching a critical line of defense. Regularly updating software
not only mitigates the risk of exploitation, but also demonstrates a
commitment to ongoing cybersecurity hygiene.
Comprehensive Disaster Recovery Plan
A comprehensive disaster recovery plan is vital for business
resilience in times of crisis. This comprehensive strategy involves
identifying critical assets and data through rigorous risk assessments,
enabling businesses to prioritize recovery efforts effectively. A
well-thought-out plan ensures that, in the face of unforeseen events,
business operations can swiftly resume with minimal downtime. Regular
data backups act as a safety net, protecting against data loss and
providing a mechanism for swift recovery.
The Journey Ahead
The journey towards enhancing network security and maintenance involves
a multifaceted approach. From staying informed through threat intelligence
to implementing advanced authentication methods, conducting security
audits, and embracing proactive monitoring and maintenance practices,
businesses can establish a robust cybersecurity framework. These measures
collectively contribute to fostering a secure digital environment,
empowering businesses to thrive in an era where cyber threats are a
constant reality.
Unveiling the Power of SentinelOne: A New Era in Endpoint Security

In a digital landscape constantly under siege from cyber threats, the
need for robust endpoint security has never been more critical. Enter
SentinelOne, a cutting-edge cybersecurity solution that has been making
waves in the industry for its innovative approach to protecting
endpoints from a multitude of threats.
Read on to learn more about SentinelOne and the following topics:
- Industry Leading Endpoint Security
- Behavioral AI for Advanced Threat Prevention
- Automated Response and Mitigation
- Complete Visibility and Forensics
Revolutionizing Endpoint Security
At the heart of SentinelOne’s prowess lies its autonomous endpoint
protection platform. Unlike traditional antivirus solutions that rely
on signature-based detection, SentinelOne leverages artificial
intelligence and machine learning algorithms to autonomously detect,
prevent, and respond to a wide array of threats. This proactive approach
enables real-time threat detection and mitigation, ensuring that
organizations can stay one step ahead of cyber adversaries.
Behavioral AI for Advanced Threat Prevention
SentinelOne’s Behavioral AI is a game-changer in the realm of endpoint
security. By continuously learning and adapting to the unique behaviors
of users and devices, this technology can identify and thwart even the
most sophisticated attacks, including zero-day exploits and fileless
malware. The ability to recognize malicious behavior, rather than just
known malware signatures, sets SentinelOne apart in an era where cyber
threats are becoming increasingly elusive.
Automated Response and Mitigation
In the face of a cyber threat, time is of the essence. SentinelOne's
automated response capabilities empower organizations to respond to
incidents in real-time. Whether it’s isolating compromised endpoints,
remediating threats or rolling back system changes, SentinelOne
ensure a swift and effective response without the need for human
intervention. This not only minimizes the impact of a security
incident but also frees up valuable resources within IT teams.
Complete Visibility and Forensics
Understanding the full scope of a security incident is crucial for
effective response and prevention. SentinelOne provides comprehensive
visibility into endpoint activities, enabling security teams to
conduct detailed forensic analyses. This visibility extends across
the entire attack lifecycle, from initial compromise to lateral
movement, facilitating thorough investigations and proactive security
measures.
The Road Ahead
As the cyber threat landscape continues to evolve, SentinelOne
remains at the forefront of innovation. Their commitment to staying
ahead of emerging threats and providing organizations with
state-of-the-art endpoint protections positions them as a key
player in the cybersecurity arena. With its advanced capabilities,
autonomous detection and swift response mechanisms, SentinelOne is
shaping a new era in endpoint security - one where organizations
can navigate the digital landscape with confidence, knowing that
their endpoints are fortified against the ever-present threat of
cyber adversaries.
Want to learn more about SentinelOne?
Give us a call at
(860) 701-0058 or
email us
for more information.
Cybersecurity Awareness Month Protecting the Digital Frontier
In our increasingly interconnected world, cybersecurity awareness has
become a paramount concern. With the proliferation of digital devices,
online services, and the vast amount of personal and sensitive data
that is stored and transmitted through the internet, the importance of
understanding and practicing cybersecurity cannot be overstated. This
newsletter will explore the significance of cybersecurity awareness,
its challenges, and the steps individuals and organizations can take
to enhance their cyber defenses.
Significance of Cybersecurity
Cybersecurity awareness is crucial because it directly impacts our
privacy, financial well-being, and even national security. The digital
realm has transformed the way we live, work, and communicate, making us
more vulnerable to a wide range of cyber threats, such as data breaches,
identity theft, ransomware attacks, and more. These threats can result
in substantial financial losses and damage to one's reputation. On a
larger scale, state-sponsored cyberattacks can disrupt critical
infrastructure and jeopardize national security.
Challenges of Cybersecurity
However, despite the escalating cyber threats, many individuals and
organizations lack the necessary awareness and knowledge to protect
themselves effectively. One of the primary challenges is the evolving
nature of cyber threats. Hackers continuously develop new tactics,
making it difficult for individuals and organizations to keep up.
Moreover, there is often a lack of motivation to invest in cybersecurity
measures until a breach occurs, even though proactive prevention is
significantly more cost-effective.
Tips to Address Challenges
To address these challenges, fostering cybersecurity awareness is
essential. This involves educating individuals about the potential
risks they face online and the steps they can take to mitigate these
risks. Here are some key areas to focus on:
- Password Hygiene: Encouraging strong, unique passwords for each online account, along with the use of two-factor authentication, can significantly enhance security.
- Phishing Awareness: Training individuals to recognize phishing emails and messages is vital to prevent falling victim to scams.
- Software Updates: Regularly updating software and devices to patch known vulnerabilities is a simple but effective security measure.
- Data Encryption: Emphasizing the importance of encrypting sensitive data, especially when it's transmitted online, helps protect against eavesdropping.
- Secure Browsing Habits: Educating individuals about the risks associated with visiting untrustworthy websites and downloading files from unverified sources is crucial.
- Social Engineering Awareness: Understanding the tactics that social engineers use to manipulate individuals into divulging sensitive information can help prevent attacks.
- Incident Response: Having a well-defined plan for responding to a cyber incident is critical to minimize damage in case of a breach.
For organizations, cybersecurity awareness extends beyond individual
practices to include comprehensive security policies, employee training,
and the implementation of robust cybersecurity measures. Additionally,
governments and regulatory bodies play a role in setting standards and
enforcing cybersecurity best practices.
Cybersecurity awareness is an indispensable component of our digital
age. It empowers individuals and organizations to defend against cyber
threats and protect their data and assets. By educating individuals
about the risks and best practices, we can create a safer online
environment. However, the landscape of cybersecurity is continually
evolving, and the commitment to ongoing education and adaptation is
crucial to staying ahead of malicious actors. Ultimately, by working
together to raise awareness and strengthen our digital defenses, we
can ensure a more secure and resilient digital frontier.
Education: Customizing Learning
The education sector is embracing AI and machine learning to customize
learning experiences. These technologies power personalized learning
platforms that adapt content and pacing to individual student needs.
Additionally, chatbots provide instant student support, and automated
grading streamlines assessment processes. Ethical concerns in education
include data privacy, as institutions must responsibly handle student
data. Ensuring fairness in algorithmic grading and transparent
communication about AI's role in education are also critical
considerations.
Have questions about how you can be more cyber secure?
Give us a call at
(860) 701-0058 or
email us
for more information.
AI and ML in Various Industries
In today's rapidly evolving technological landscape, Artificial
Intelligence (AI) and Machine Learning (ML) have emerged as
transformative forces, reshaping industries across the board.
From healthcare to finance, transportation to retail, these
intelligent technologies are finding applications that were once
considered science fiction, ushering in breakthroughs that hold
the promise of unparalleled progress and efficiency. Yet, as we
embark on this journey into an AI-driven future, it's crucial to
navigate the path with a vigilant eye on ethical considerations,
ensuring that these powerful tools are wielded responsibly, fairly,
and transparently. In this exploration, we embark on a journey
through the diverse applications, groundbreaking achievements,
and the ethical compass guiding AI and ML adoption in various
industries.
Healthcare: Revolutionizing Patient Care
In healthcare, the applications of AI and machine learning are
transforming the way we diagnose and treat diseases. AI-powered
diagnostic tools are becoming increasingly accurate, enabling early
detection of conditions such as cancer and heart disease.
Breakthroughs in medical imaging, using deep learning algorithms,
have allowed for the identification of abnormalities in X-rays,
MRIs, and CT scans with unprecedented precision. However, ethical
considerations abound in healthcare, particularly concerning patient
data privacy and the potential for algorithmic biases to affect
diagnosis and treatment recommendations. It's essential to strike
a balance between technological advancement and maintaining patient
trust and safety.
Finance: Redefining Financial Services
The financial industry is experiencing a digital revolution, with
AI and machine learning at the forefront. These technologies are
being used for fraud detection, where AI algorithms analyze vast
datasets in real-time to identify and prevent fraudulent transactions.
Additionally, algorithmic trading, powered by machine learning, can
optimize investment strategies. Nevertheless, ethical considerations
in finance are substantial, including concerns about algorithmic
transparency and the potential for automated decisions to perpetuate
biases. Ensuring fairness and data security is crucial to building
trust in AI-driven financial services.
Transportation: Navigating the Future
In transportation, AI and machine learning have paved the way for
autonomous vehicles, revolutionizing the way we travel. Self-driving
cars, a major breakthrough, rely on machine learning models to
navigate and make real-time decisions on the road. Predictive analytics
also play a role in traffic prediction and route optimization, reducing
congestion and fuel consumption. However, safety remains a paramount
concern, and addressing ethical dilemmas, such as determining how
autonomous vehicles make decisions in critical situations, is an ongoing
challenge.
Retail: Personalizing Shopping Experiences
The retail industry is leveraging AI and machine learning to provide
highly personalized shopping experiences. Recommendation engines,
powered by machine learning algorithms, analyze customer behavior to
suggest products tailored to individual preferences. This breakthrough
enhances the shopping experience and boosts sales. Ethical considerations
here center on data privacy, as retailers must ensure that customer
data is protected and used responsibly. Balancing personalized service
with privacy is essential to maintain customer trust.
Manufacturing: Boosting Efficiency
In manufacturing, AI and machine learning are improving efficiency and
reducing downtime. Predictive maintenance, a notable application, uses
AI to analyze equipment data and predict when maintenance is needed,
preventing costly breakdowns. Automation and robotics are also on the
rise, enhancing productivity. However, ethical considerations revolve
around workforce displacement. It's vital for manufacturers to invest
in reskilling and upskilling their workforce to mitigate job losses and
ensure a smooth transition to automated processes.
Education: Customizing Learning
The education sector is embracing AI and machine learning to customize
learning experiences. These technologies power personalized learning
platforms that adapt content and pacing to individual student needs.
Additionally, chatbots provide instant student support, and automated
grading streamlines assessment processes. Ethical concerns in education
include data privacy, as institutions must responsibly handle student
data. Ensuring fairness in algorithmic grading and transparent
communication about AI's role in education are also critical
considerations.
Energy: Greening the Grid
AI and machine learning are playing a pivotal role in the energy
sector's transition to sustainability. Grid optimization algorithms
balance energy supply and demand efficiently, reducing waste and carbon
emissions. Renewable energy management systems leverage predictive
analytics to maximize the generation of clean energy. Ethical
considerations center on transparency in energy management decisions
and the environmental impact of AI-driven decisions.
Legal and Compliance: Streamlining Legal Processes
In the legal and compliance sector, AI and machine learning are
streamlining processes such as document review, legal research, and
contract analysis. These technologies can quickly sift through vast
volumes of documents, aiding legal professionals in their work. Ethical
considerations encompass maintaining accuracy and fairness in AI-assisted
legal decisions and ensuring data privacy during legal proceedings.
In each of these industries, the applications and breakthroughs brought
about by AI and machine learning hold great promise. However, addressing
ethical considerations is essential to harness the full potential of
these technologies while maintaining trust and fairness within society.
Interested in delving deeper into the realms of AI and machine learning?
Give us a call at
(860) 701-0058 or
email us
for more information.
Is there a difference between memory and storage?
When buying a new computer or phone, there are tons of terms that
may be thrown at you, such as SSD, HDD, ram, CPU, etc. In the world
of tech, these terms are widely known, but for some people, these
abbreviations may confuse them and have them questioning whether a
laptop or desktop is a good choice or not.
So what do these terms refer to?
Depending on what abbreviation you’re looking at, they could be
referring to what’s called memory or storage.
So, what’s the difference between memory and storage on a new
workstation?

Memory or RAM is where the computer stores the information it’s currently using. It makes it so that the CPU, or central processing unit, has almost instantaneous access to all of the information there, no matter where it is actually stored. It’s designed to keep your computer or smartphone working fast, depending on the amount of RAM your system has. The more RAM in the system, the faster it will be. When a computer turns off, memory loses data, making it temporary and volatile.

Storage is where your computer or your smartphone stores information
permanently. This allows your information to be easily accessible and
includes your pictures, documents, text messages and music that you
have saved. Smartphones and most computers use SSDs, or solid-state
drives, which store information using transmitters that can maintain
a charge even when they are turned off. Some older computers may use
HDDs, or Hard disk drives. HDDs have a physical platter where information
is stored.
For the most part, SSDs are faster than HDDs since there are no
moving parts. You may get an instant boost in performance if you were
to upgrade your HDD to an SSD.
Now that we know what the difference is between memory and storage,
buying a new smartphone or computer will be a breeze.
Have a question about whether a computer may be a good buy or not or
just want some clarification on an IT term you aren’t familiar with?
Give us a call at
(860) 701-0058 or
email us
for more information.
What is Data Loss and how much does it cost?

Data loss refers to the unintentional or accidental destruction, corruption,
or loss of data stored on digital devices or systems. It occurs when data becomes
inaccessible, unreadable, or permanently deleted, leading to its irretrievable
loss.
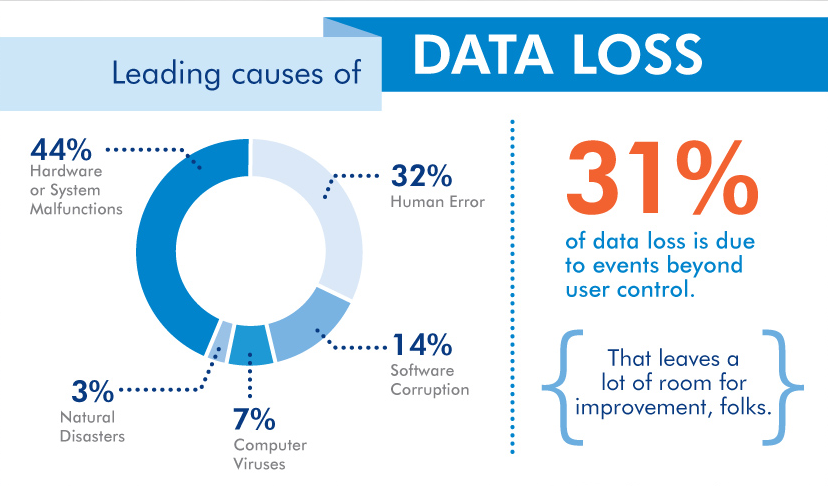
Data loss can happen due to various reasons, including hardware or software
failures, human errors, malware or ransomware attacks, natural disasters, power
outages, theft, or intentional deletion.
Data loss can have significant consequences, including financial
losses, legal issues, operational disruptions, reputational damage,
and the loss of valuable or sensitive information. It highlights
the importance of implementing data backup strategies, using data
recovery techniques, and maintaining robust security measures to
minimize the risk of data loss and ensure data integrity.
The cost of data loss can vary widely depending on several factors, including the size and type of organization, the extent of the data loss, the nature of the data, and the industry in which the organization operates. Here are some of the potential costs associated with data loss.
- Lost productivity: When data is lost, it can result in downtime and interruptions to business operations. Employees may be unable to access critical information, leading to decreased productivity and delayed projects.
- Data recovery and restoration: Attempting to recover lost data can be a complex and costly process. It may require specialized expertise and the use of data recovery services or software.
- Re-creating or re-collecting data: In some cases, lost data may need to be re-created or re-collected, which can be time-consuming and resource-intensive.
- Financial impact: Data loss can have direct financial implications, such as lost sales, missed business opportunities, or contractual penalties. It can also result in the loss of intellectual property, trade secrets, or sensitive customer information, leading to potential legal and regulatory costs.
- Reputational damage: Data breaches or data loss incidents can erode customer trust and damage a company's reputation. Rebuilding trust and recovering from reputational damage can be challenging and may require additional investments in marketing and public relations efforts.
- Regulatory non-compliance penalties: Depending on the industry and geographical location, organizations may be subject to data protection regulations and face penalties for failing to safeguard customer data adequately.
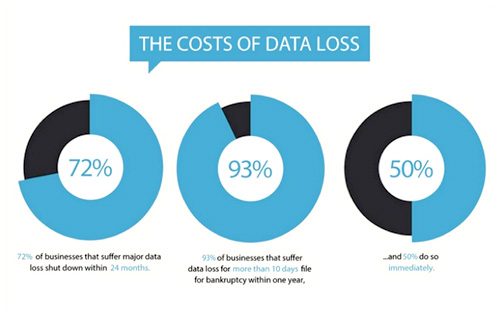
It is difficult to estimate an exact cost of data loss as it
varies from case to case. However, studies and surveys have shown
that data loss incidents can be extremely costly for organizations,
ranging from thousands to millions of dollars, considering the
direct and indirect expenses associated with data recovery,
business disruption, legal actions, and reputational damage.
To mitigate the financial impact of data loss, organizations
should invest in robust data backup solutions, implement effective
data security measures, and develop a comprehensive incident
response plan to minimize the risk and consequences of data loss
incidents.
Visit us on Facebook
for tips and tricks on how to manage data
loss and other security awareness topics.
Give us a call at
(860) 701-0058
if you have further questions on this topic.
How secure are your accounts?
Imagine you stay home from work and decide you want to get some
work done so you aren’t overloaded when you get back. You plug in
your login information for your Outlook and your emails pop up. Well,
that was easy! Now, who’s to say you’re the only one trying to get
into that account or even your computer? Hackers are constantly
trying to one up all of our security measures. And if you don’t
have any in place, then you’re essentially giving them your
information for free.
With Multifactor Authentication, or MFA, you have an added security
barrier blocking out the bad guys from stealing your information.
But know, not all MFA are created equal.
These same hackers are finding ways around certain MFA setups. An
easy example is if you have MFA setup, but the prompts have you
click yes or no to allow you in. With how fast paced the world is
today, many people don’t have the luxury of time. So, when the prompt
comes up and you just want to get it out of the way, you may push
yes and unknowingly allow someone to access your account without
your consent.
So, what MFAs are safe for you to use?
There are so many options out there today, but picking one that has
you stop to think about what you’re doing is one of the safer options.
Needing to type in a code or a password is a better way to secure your
account against these hackers.
Not sure how to make your MFA more secure than it already is? Our
team is happy to walk you through changing your MFA and security
settings so that you have peace of mind knowing your accounts are
safe.
Watch the video below made by our Engineer Brian Mayo to learn
what he has to say about MFA.
Give us a call at (860) 701-0058 if you have further questions on this topic.
Security Awareness
With security being a top priority for most businesses, we want to take this month’s newsletter and discuss some ways to keep your business secure. Cybercriminals are developing new ways to steal your information, making it hard to know when or what they are going to do next. Here are a few tips on how you can keep your information in your hands.
- Setup a multi-factor authenticator app so that only you have access to your accounts. Don’t automatically click yes or no when it asks about a sign in. We know it may be a force of habit, but cybercriminals are now trying to sneak past the authentication when it is sent to your phone. Changing what kind of multi-factor authentication you use is a beneficial tool to help break the habit of accepting the authentication.
- Use a password manager to store your passwords. With this app, you have the ability to set highly encrypted passwords and store them away for future use. You no longer have to write them on a sticky note or save them on the webpages. Bitwarden is a great example of a password manager.
- Be careful about opening up emails. Always check for any signs it may be a phishing email. Use the SLAM method to evaluate emails. Not sure what that is? Give us a call and we can discuss it! Breach Secure Now is a great platform to learn about phishing emails and how to know if you are sent one.
- Did you know that if you hover over the sender in an email, it will show you who actually sent the email? This is a good way to figure out if the sender is legit or if you could possibly be looking at a phishing email. You can do the same thing for links, even if they say click here or are a button.
- Microsoft won’t call you to tell you something is wrong with your computer. If you get a call from someone that’s claiming to be from Microsoft, hang up. Do not give them your information.
- If a screen pops up on your computer saying there’s an issue or that there’s ransomware on your computer, shut your computer off and call your IT department. We will help you figure out if this is spam and what you should do to safely get rid of it.
Remember: If you ever have any reservations that there may be something wrong with your security or you need help determining if an email is real, give us a call at (860) 701-0058 so we can work with you to solve it.
Are you Cyber Smarter than a fifth grader?
Cybercrimes are becoming more and more common as the days go on. As
technology improves and people become more aware of scams going around,
cybercriminals are working on new ways to get your information. What
you may hear today, may be irrelevant tomorrow.
Thankfully, there are many tips and tricks to help you stay vigilant
and save your information from being bought and passed around. Find
out some tips and tricks by clicking the button below and reading
more about how to keep your information away from others. If you
have any questions or concerns regarding how you may be affected by
cyber scams, please
reach out to us.
>
Cyber Security Tips
Are you looking for an MVP?
With recent advances in technology and an increase of people working
away from their desk, having equipment you can take on the go with you
has become a necessity. Luckily for you, Dynamic Alliance has partnered
with RingCentral to bring you a new solution to working from home or
on the go.
RingCentral is an industry-leading platform for cloud communications,
empowering organizations to streamline internal collaboration and better
connect with their customers. From phone calls to texting and sending
faxes, RingCentral has made it easy to communicate with your clients
from anywhere at any time. Workers at remote locations or home offices
are connected the same way employees working in the main corporate
office are, with the RingCentral app. It can transform a mobile phone
into a desk phone and powerful communications device with a few taps.
>
Learn more about the features you can expect
when you switch to RingCentral
RingCentral Fax
It may be a dying technology, but many businesses still use faxing
capabilities to be HIPAA and other security agency compliant. With
RingCentral fax, you can rest easier knowing cloud fax securely
transmits over an encrypted internet connection.
Thanks to the cloud-based phone system, you can receive faxes anywhere
at any time, send faxes online to groups, block faxes without caller
ID, and receive fax notifications of all activity with ease from
computers, cell phones and tablets. There’s no need to worry about
being on the phone or loading paper into the printer, you’ll still
seamlessly receive your fax messages through the mobile or desktop app.
>
Take a peek to learn more about how RingCentral
will benefit your business
Exploring Cybersecurity Opportunities
Do you know what phishing is? What about spoofing? Deepfakes? With the
uptick in cybersecurity threats making themselves known, now is a good
time to make employees of your business aware of potential threats a
simple click on an email or link follow can have on the security of your
business. Thankfully, Dynamic Alliance has partnered with Breach Secure
Now to help train and bring awareness to avoid phishing, spoofing, and
other cybersecurity threats.
Breach Secure Now, or BSN, is a partner focused business who works for
the MSP community to provide clients with the most comprehensive
cybersecurity solutions. Through Cybersecurity and HIPAA Compliance
Training made easy to automate, support, and empower, employees can
become the superhuman firewall every business needs. Weekly training
is provided to businesses so that everyone can receive the power of
knowledge on how to prevent cybersecurity threats from taking over the
day to day of businesses. With automated phishing campaigns, you can
find out who is most susceptible to these threats. The ongoing training
programs and campaigns allow you get instant insight to your employees’
scores with the easy-to-understand Employee Secure Score (ESS).
Businesses are able to monitor the dark web through BSN to monitor what
information has been compromised to ensure the safety of employees’ logins
and information. Without continuous monitoring, new compromised employee
data available on the dark web will go unnoticed, putting your employees
and yourself in danger of dealing with a data breach. Compromised passwords
increase the risk of external access to your employees' networks. Exposed
personally identifiable information (PII) opens the door to convincing
phishing attempts. With data breaches on the rise, unnoticed activity on
the dark web puts organizations at risk. With real-time updates, detailed
breached data, and remediation ready to deploy all at your fingertips,
employees can stay secure and protected from the repercussions of data
breaches.
Contact Dynamic Alliance today to learn more on how you can
protect your business against Cybersecurity threats.